IPSEC VPN
IP Security (IPSec)VPN provides the most robust remote access environment to remote users by
extending almost any data,voice,or video application available in the office to remote working
locations. IPSec VPN client software on the remote system enables a user experience and workflow
consistent with the office environment by providing easy application access and system integrity
enforcement. IPSec VPN provides the most comprehensive level of network access to remote users,thus
extending the productivity ofthe office to virtually any location.This "any application access" has
made iPSec VPN the defacto standard for extending connectivity to home offices,traveling employees,
remote workers,and day extenders.
Remote Access VPNs
Corporations useVirtuel Private Networks (VPNs) to establish secure, end-to-end private network
connections over a public networking infrastructure.VPNs have become the logical solution for
remote access connectivity.Deploying a remote access VPN enables corporations to reduce
communications expanses by using the local dialup infrastructures of Internet Service Providers. At
the same time,VPNs allow mobile workers,telecommuters,partners,and day extenders to take advantage
of broadband connectivity.To fully realize the benefits of high-performance remote access VPNs, a
corporation must deploy a robust, highly available VPN solution,supporting both IPSec end WebVPN
(clientless) capabilities.
Consider the following scenario.Remote users need to dial into the corporate office end
access e-mail, corporate presentations,order entry,and engineering. ln addition, Corporate
Information Services wants remote users to access corporate resources fast, inexpensively, and as
securely as possible.
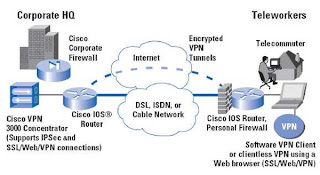
lmplementing a remote-access virtual private network (VPN) with the Cisco VPN 3000
Series Concentrator and the CiscoVPN Software Client is the right choice. It enables remote users to
access the corporate resources they require. Corporate Information Services meets their
speed, expense, and security requirements.
The Client-tc-LAN VPN consista of four componente: IPSec client software, Point-to-Point
Protocol (PPP), IPSec standards, and the Concentrator.
• IPSec client software- The IPSec client software is not native to the Microsoft
Windows operating system and must be loaded on the PC. lt is used to encrypt, authenticate,and
encapsulate data. lt aIso terminates one end of the tunnel.
• PPP- For remote access applications, the PC relies on PPP to establish a physical connection to
the local ISP or the Internet.
• IPSec standards- After the ISP authenticates the remote user,the user launches the IPSec client
IPSec establishes a secure tunnel or session through the Internet to the Concentrator.
• Concentrator- The Concentrator terminates the opposite end of the tunnel.The
Concentrator decrypts, authenticates, and de-encapsulates the data.
The Software Client works with the Concentrator to creete a secure connection, called a
tunnel, between your computer and the private network. lt uses Internet Key Exchange
(IKE) and IPSec tunneling protocols to make and manage the secure connection.
Some of the operations that the Software Client performs, which are mostly invisible to you, inctude
the following:
• Negotiating tunnel paramaters: addresses, algorithms, lifetime,and so on
• Establishing tunnels according to the parameters
• Authenticating users by ensuring that users are who they say they are through usenames,group
names, passwords,and digital certificates
• Establishing user access rights: hours of access,connection time, allowed destinations,allowed
protocols,and so on
• Managing security keys for encryption and decryption
• Establishing the IPSec session
Authenticating,encrypting, and decrypting data through the tunnel.
Thanks for reading and commentting!!!!

Aucun commentaire:
Enregistrer un commentaire
Nom
Prénom